The significance of data privacy for data-driven industries has reached a level that businesses can no longer afford to overlook. While information is at the core of product and service development for many companies, legality, and corporate considerations have been exerting mounting pressure on these sectors. Regulators, citizens, and the escalating frequency of cybersecurity incidents have compelled companies to embrace more resilient privacy protection methodologies.
Various techniques aimed at enhancing privacy have undergone refinement to meet the escalating demands driven by both technical advancements and societal expectations. Frequently, the focus is on safeguarding personal data when it comes to companies implementing privacy measures. Nevertheless, any form of sensitive data may necessitate privacy protection. This includes various types of business information, such as financial data or trade secrets, which may require confidentiality to ensure their security.
Businesses, organizations, and individuals alike are forced to adopt robust data protection methods to ensure the confidentiality and integrity of sensitive information. The current challenge lies in determining the most appropriate approach to adopt.
Various privacy protection techniques provide distinct levels of safeguarding. It is crucial to be acquainted with and comprehend their functionalities. Depending on the application's nature and the type of data involved, companies can opt for a specific technique.
Encryption
Encryption is a fundamental technique that transforms data into unreadable code, making it indecipherable. Concealing sensitive data often involves employing a cipher secured by an encryption key. This technique ensures that the information remains confidential by encoding it with a cryptographic algorithm and can only be deciphered by possessing the corresponding encryption key.
Utilizing strong encryption algorithms is crucial for protecting data during transmission and storage, ensuring that even if unauthorized access occurs, the information remains secure.
Tokenization
Tokenization is a robust technique that enhances privacy by substituting sensitive data with unique tokens or symbols. Unlike traditional anonymization methods, tokenization retains the structural format of the original data without revealing its actual content. This process involves generating a unique token for each piece of sensitive information, such as credit card numbers or personal identifiers.
Data masking
Data masking involves concealing specific portions of sensitive information, such as partially or completely hiding characters in an email address or credit card number. This technique is valuable for creating realistic but anonymized datasets for testing or development purposes.
Differential privacy
Differential privacy focuses on adding noise or randomization to data, making it challenging to discern the contribution of any individual data point. This method is particularly relevant in scenarios where aggregated information is needed while protecting the privacy of individual contributors.
However, there is a "but"... some of these methods are not 100% reliable in current scenarios. For example, achieving perfect anonymization in data is seldom possible, as it would essentially render the data nearly useless. Other methods, like data masking, complicate the identification of individuals but don't eliminate the possibility of re-identifying someone entirely.
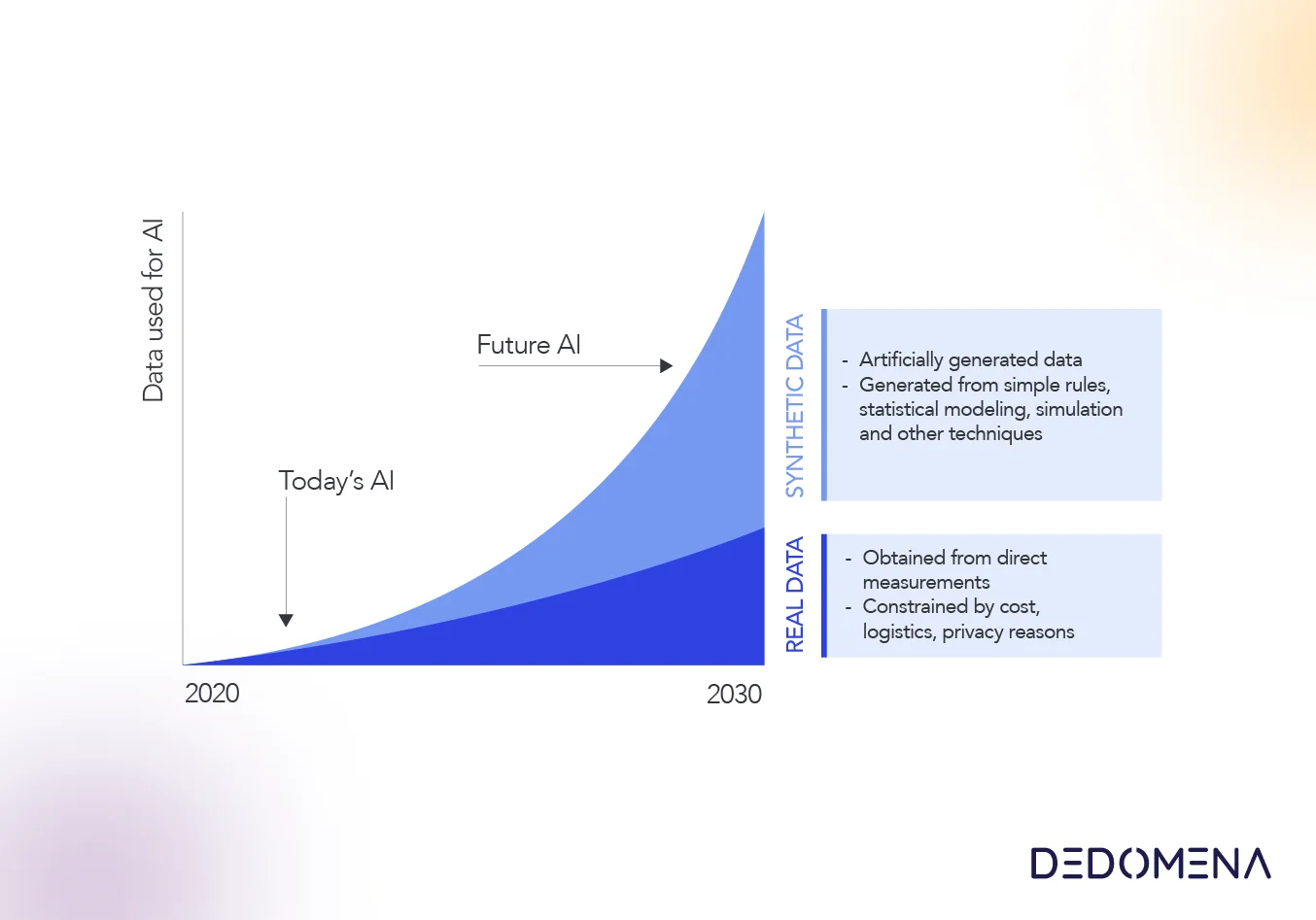
Synthetic data, overcoming the limitations of traditional methods
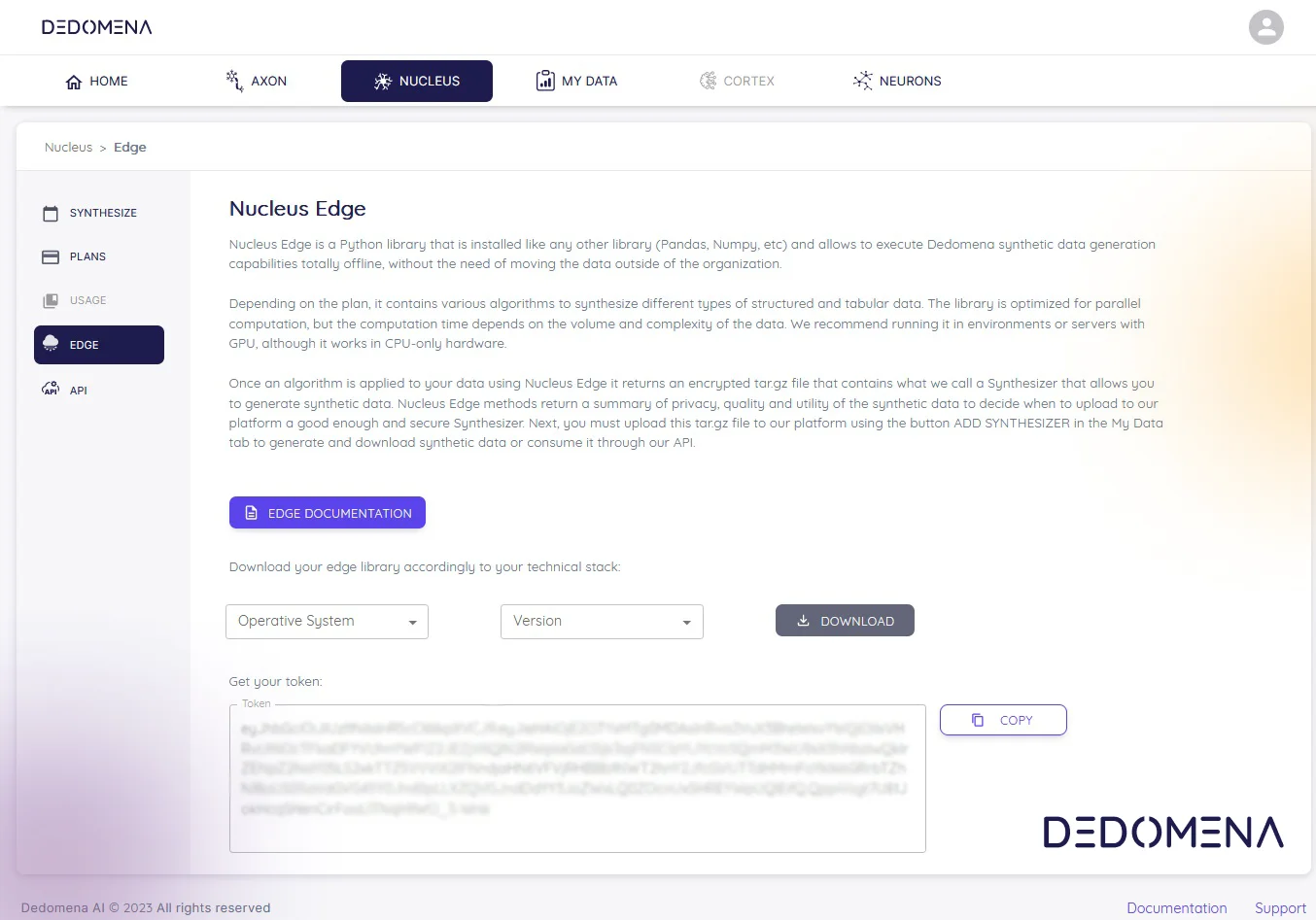
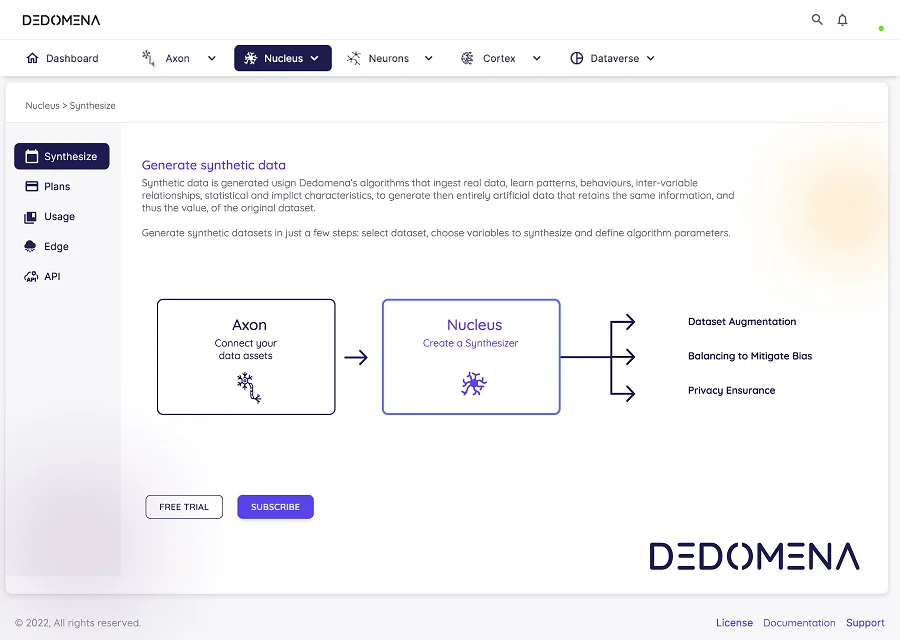
Synthetic data presents a distinctive paradigm in the realm of privacy protection, providing a nuanced approach to striking a balance between the inherent shortcomings of other methods when it comes to data privacy and data utility. Rather than resorting to the conventional methods of altering or masking original data, this approach involves the generation of entirely new, artificial data. Leveraging machine learning models, this innovative technique facilitates the creation of a synthetic dataset that closely mirrors the statistical properties of the original data.
By opting for synthetic data, organizations can maintain privacy without compromising the integrity of the information. The generated dataset, although artificial, retains the essential characteristics of the real data, providing a practical and privacy-preserving solution for various applications. This methodology not only complicates attempts at unauthorized access but also ensures a more robust defense against potential re-identification of individuals, thereby addressing some of the inherent challenges posed by traditional privacy protection methods.
The challenge lies in ensuring that the synthetic data not only preserves the statistical properties of the original dataset but also captures the nuances introduced by outliers or unique data instances. Therefore, careful consideration and validation are imperative in the selection and implementation of synthetic data generation methods to mitigate the risk of inaccuracies and potential compromises in utility.